We’ve outlined 14 critical steps you should take to protect your company’s computers from criminal hackers.
What is ransomware?
Ransomware is exactly what it sounds like: malicious software created to infect your computer and restrict access until you pay a ransom. The attacker will attempt to extort a ransom by displaying an on-screen message that tells the victim that his or her files have been encrypted. The victim will also be notified that unless that ransom is paid, access will be irreversibly revoked; meaning everything stored within that computer will be gone forever. According to the US-CERT, The typical ransom that is demanded varies significantly based on certain factors but is typically $200-$400 and is only payable in digital cryptocurrency, such as Bitcoin (BTC).
How does ransomware get onto someone’s computer?
The most common method for spreading ransomware is via phishing emails that contain either malicious attachments or redirects to a site that will download and install the malware on your computer without your knowledge. As these types of attacks have matured, however, criminal hackers have become much craftier in spreading their software. It’s not unusual now to see social media posts or instant messages that contain links to malicious content, so exercise caution when clicking on something that you aren’t familiar with.
Why is ransomware so effective?
This type of malware is effective for a couple of reasons: the first being fear and panic, the second being the fact that the entirety of the victims files are completely encrypted and theoretically lost until the ransom is paid. These two factors together make ransomware a very effective form of malware that can fund the criminal hacking operation far into the future.
What does ransomware look like?
A ransomware infection may resemble any of the below images:

An infection claiming to be an FBI lockdown.
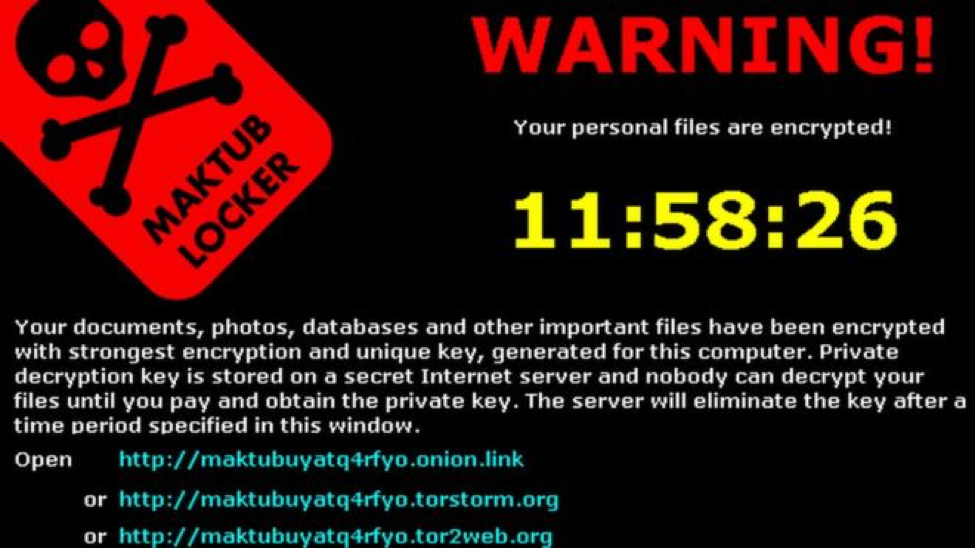
The “Maktub Locker” ransomware.
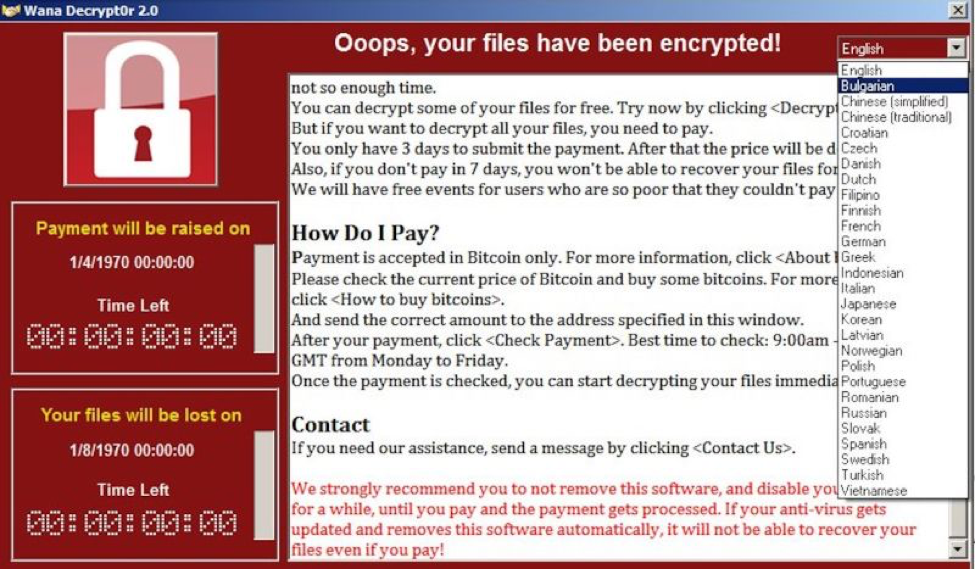
The “Wana Decrypt0r,” also known as “WannaCry” or “WannaCrypt.”
Some common examples of ransomware messages:
- “Your computer was used to visit websites with illegal content. You must pay a $100 fine to regain access.”
- “All files on your computer have been encrypted. You must pay this ransom within the timeframe below or else you will lose your data forever.”
- “Your computer has been infected with a virus. Click here to resolve the issue.”
How ransomware impacts businesses
Businesses are often the target for such attacks, since it is much more likely that the attacker will encrypt valuable company assets and therefore have a better chance at getting paid the ransom. Some negative consequences include:
- Temporary or permanent loss of sensitive or proprietary information
- Financial losses due to recovery and restoration efforts
- Disruption to operations, department or company-wide downtime
- Harm to an organization’s reputation if sensitive data has been leaked or lost
- Undue stress and anxiety for employees of an infected organization
Paying the ransom will not guarantee that the encrypted files will be released. In fact, it only guarantees that the criminal receives the victim’s money, and even their banking information in some cases. Additionally, the malware infection itself could still remain after the files have been decrypted.
14 steps for minimizing your risk of being a ransomware victim
The US-CERT and Liberteks discourage victims from paying any ransom, as the encrypted files are not guaranteed to be released. You should report instances of fraud to the FBI at the Internet Crime Complaint Center. Liberteks encourages end users and system administrators to take the following preventative measures to protect their computers and networks from ransomware:
- Employ a data backup and recovery plan for all critical information. Perform and test regular backups so that you can expedite the recovery process. Network-connected backups can also be affected by ransomware, so ensure that critical backups are isolated from the network for complete protection.
- Make use of application whitelisting to prevent any malicious software or unapproved programs from running.
- Make use of a strong antivirus program, and keep that program up-to-date. Scan any software downloaded from the internet prior to executing.
- Keep your operating system and applications completely up-to-date with the latest patches and updates. Vulnerable operating systems and applications are one of the biggest targets for malware.
- Restrict user permissions so that unwanted software can’t be installed or run.
- Don’t click on web links in suspicious or unsolicited emails.
- Try to avoid enabling macros from email attachments. For organizations, it is best to block emails that contain attachments from suspicious sources.
- Train your employees with an awareness program. End users are common targets, so it’s important that they’re aware of the threat and how it is commonly delivered.
- Make use of strong spam filters to prevent phishing emails from reaching employees. Authenticate inbound emails using a common technology like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Indentified Mail (DKIM) to prevent any email spoofing.
- Configure your firewalls to block access to any known malicious IP addresses.
- Set a scanning filter on inbound and outbound emails to block the transmission of executable (exe) files.
- Ensure that your antivirus program is set to scan regularly. We recommend that you set a daily scan at a time that you are away from the computer.
- Configure access controls on your network and storage, keeping the bare minimum privilege in mind. If an employee only needs read access, then only grant them read access. Malicious software will be able to modify files where write permissions are granted.
- Don’t give everyone an administrator account, and restrict use of admin accounts to the times that it’s absolutely necessary. Use restricted accounts regularly to prevent malware from gaining uninhibited access to your files, network and shared locations.
As always, we encourage you to give our team a call so that our trained personnel can implement these steps at your home or organization. With over 26 years in IT security, our team knows exactly what’s needed to protect your systems from criminal hackers both at home and abroad.
Call 518-452-0550 x1 to schedule your professional security service today. We look forward to working with you.
-The Liberteks.com Team
See the US-CERT publication on ransomware here.



















